Amazon will not say if it plans to take action against three phone surveillance apps that are storing troves of individuals’ private phone data on Amazon’s cloud servers, despite TechCrunch notifying the tech giant weeks earlier that it was hosting the stolen phone data.
Amazon told TechCrunch it was “following [its] process” after our February notice, but as of the time of this article’s publication, the stalkerware operations Cocospy, Spyic, and Spyzie continue to upload and store photos exfiltrated from people’s phones on Amazon Web Services.
Cocospy, Spyic, and Spyzie are three near-identical Android apps that share the same source code and a common security bug, according to a security researcher who discovered it, and provided details to TechCrunch. The researcher revealed that the operations exposed the phone data on a collective 3.1 million people, many of whom are victims with no idea that their devices have been compromised. The researcher shared the data with breach notification site Have I Been Pwned.
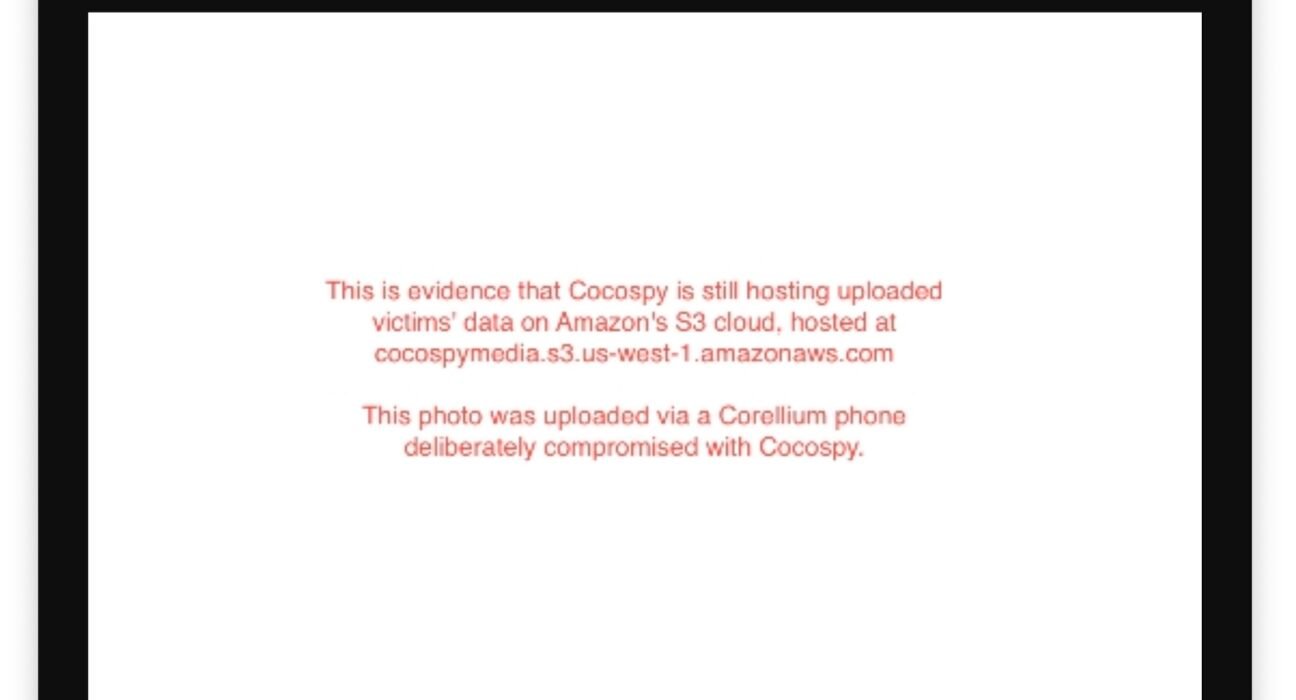
As part of our investigation into the stalkerware operations, which included analyzing the apps themselves, TechCrunch found that some of the contents of a device compromised by the stalkerware apps are being uploaded to storage servers run by Amazon Web Services, or AWS.
TechCrunch notified Amazon on February 20 by email that it is hosting data exfiltrated by Cocospy and Spyic, and again earlier this week when we notified Amazon it was also hosting stolen phone data exfiltrated by Spyzie.
In both emails, TechCrunch included the name of each specific Amazon-hosted storage “bucket” that contains data taken from victims’ phones.
In response, Amazon spokesperson Ryan Walsh told TechCrunch: “AWS has clear terms that require our customers to use our services in compliance with applicable laws. When we receive reports of potential violations of our terms, we act quickly to review and take steps to disable prohibited content.” Walsh provided a link to an Amazon web page hosting an abuse reporting form, but would not comment on the status of the Amazon servers used by the apps.
In a follow-up email this week, TechCrunch referenced the earlier February 20 email that included the Amazon-hosted storage bucket names.
In response, Walsh thanked TechCrunch for “bringing this to our attention,” and provided another link to Amazon’s report abuse form. When asked again if Amazon plans to take action against the buckets, Walsh replied: “We haven’t yet received an abuse report from TechCrunch via the link we provided earlier.”
Amazon spokesperson Casey McGee, who was copied on the email thread, claimed it would be “inaccurate of TechCrunch to characterize the substance of this thread as a [sic] constituting a ‘report’ of any potential abuse.”